How does our system work?
In critical environments such as medicine and defense, it's not enough to fill in a document with any value — it is essential to ensure that only combinations previously approved by a higher authority can be used. Our system enables the creation of documents with dynamic fields (placeholders), where valid combinations are digitally signed using RSA or authenticated using HMAC, ensuring:
- Integrity of the document's content
- Local cryptographic validation without requiring online reauthentication
- Automatic rejection of unauthorized combinations
Tip: To ensure your document can be signed securely, use square brackets to define
authorized placeholder options. For example:
[Name: Leonardo, Tiago, Ricardo] or Acquisition: [OsLicence: CentOS, NixOS, RedHat].
These will be interpreted as valid and signable combinations. On the other hand,
free text fields are not signed and should only be used for non-critical data.
Important: Do not use spaces in the placeholder name (e.g., use
UserName instead of User Name), otherwise the system will not be able
to generate a valid signature for that field.
Use Case 1: FDA-validated medical prescription
An oncologist intends to prescribe an aggressive treatment to a patient — for instance, a monoclonal antibody developed by Roche Pharmaceuticals. However, this treatment can only be used if it has been pre-approved and digitally signed by the FDA. The system ensures that:
- The doctor can only issue the prescription if the selected option is validated by the FDA's signature
- Any attempt to tamper with the content (e.g., by a man-in-the-middle attacker) is detected and blocked
- The patient receives only validated and authorized prescriptions

Use Case 2: Military procurement with high-assurance validation
A military officer submits a request to acquire encrypted communication modules from Northrop Grumman, a major U.S. defense contractor. All possible valid combinations (e.g., model, quantity, purpose) are pre-signed by a superior military authority, such as the U.S. Department of Defense. The system guarantees that:
- Only approved options can be submitted for procurement
- An attacker (internal or external) cannot inject invalid combinations since they cannot sign them
- This reduces the risk of sabotage, operational failure, or threats to national or organizational security

Attack Diagram
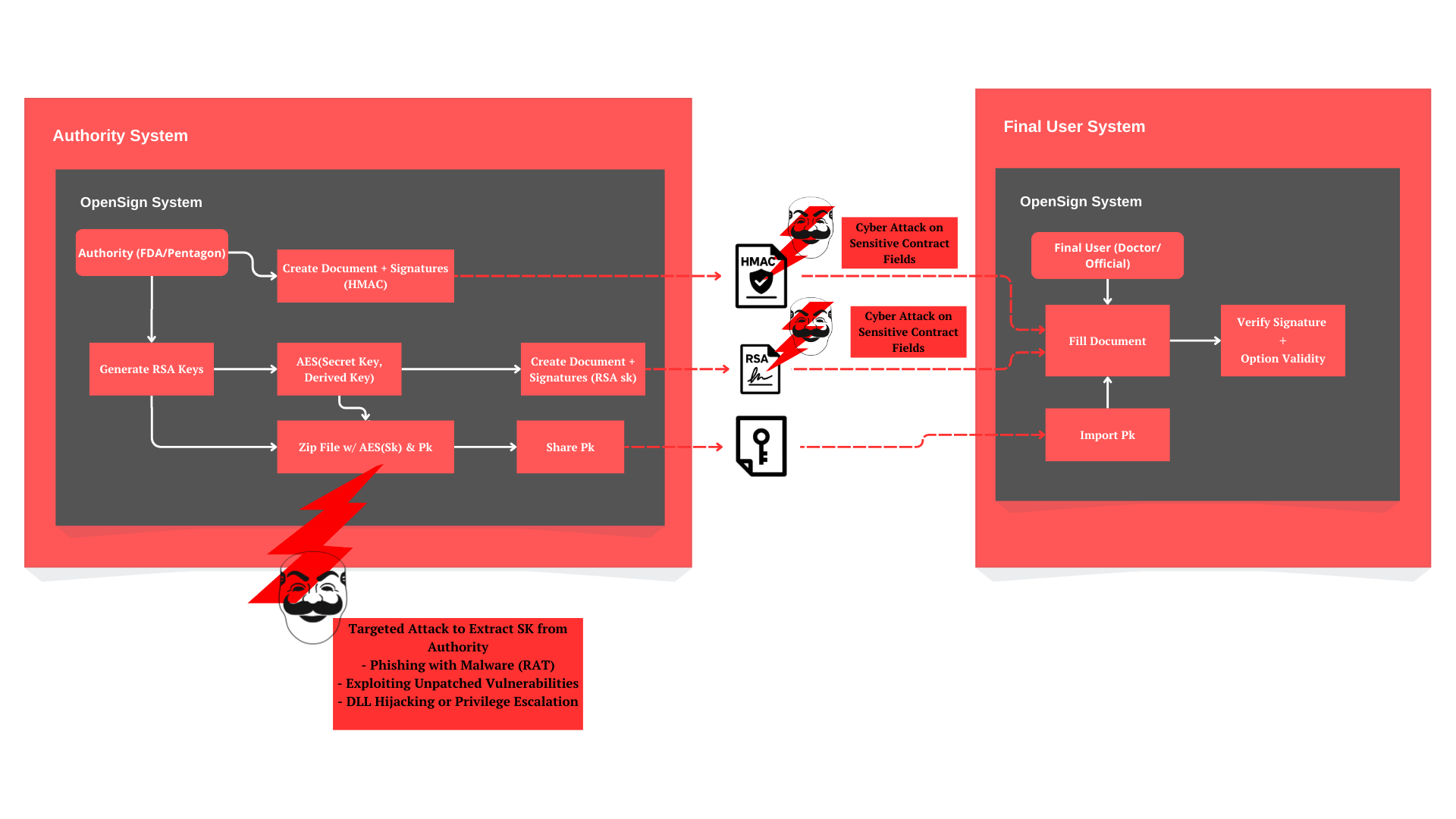
The OpenSign system is designed to ensure that digital documents containing placeholders or multiple-choice fields can be securely signed — even in highly sensitive contexts like healthcare, legal contracts, or government approvals.
With a combination of RSA digital signatures, AES-256 encryption for protecting private keys, and secure placeholder validation, OpenSign guarantees document integrity and authenticity even if attackers attempt to manipulate the content.
- Private keys are encrypted using AES-256 and a password-derived key (HMAC-SHA256);
- Each valid placeholder combination can be individually signed to prevent unauthorized completions.
Even in the event of a targeted system breach (e.g., through malware or privilege escalation), any forged or altered documents will fail validation by end users. OpenSign protects trust, privacy, and digital integrity.
System Diagram
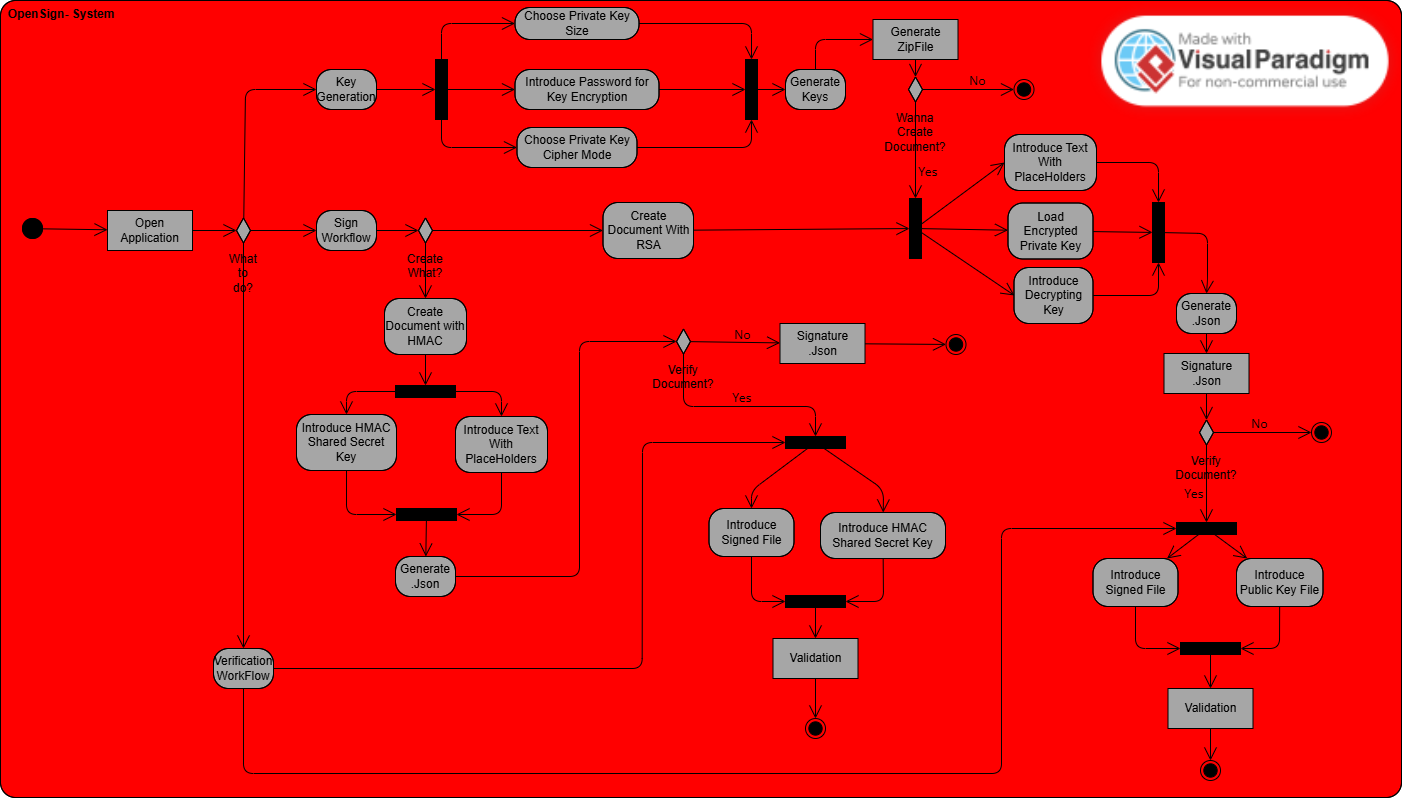
The following diagram illustrates the end-to-end flow of the OpenSign application, from RSA key generation to final document validation. It outlines how secure document creation and cryptographic protection are handled step-by-step by the system.
This flowchart was modeled using Visual Paradigm, adhering to a structured methodology inspired by Polish system modeling practices. The style follows the teachings of Dr. Małgorzata Maria Żabińska-Rakoczy from the AGH University of Science and Technology in Poland. Some members of the OpenSign development team had the opportunity to maintain contact with her through academic exchange, and her recommendations—particularly regarding system abstraction and validation-centric architecture—greatly influenced this diagram.
- Users generate RSA key pairs with AES-256 encryption using a password-derived key.
- Documents are authored with placeholders supporting free text and multiple-choice options.
- Valid placeholder combinations are digitally signed (RSA) or authenticated (HMAC).
- Document validation ensures only authorized content is accepted by verifying the cryptographic signatures.
This visual model helps supervisors, reviewers, and auditors clearly understand the system's secure workflow and layered defenses.
Did you enjoy our work?

Through OpenSign, we strive to promote a safer and more transparent digital world. Our goal is to empower individuals and organizations to protect their data, their integrity, and their right to privacy — one signature at a time. We believe in building trustworthy tools that respect ethical values and help shape a more secure cyberspace for everyone.
If you would like to get in touch with the team lead or have any questions, feel free to reach out via email.
📧 Contact the Team Lead